am 07.07.2025 - 13:04 Uhr
Hacker attacks on buildings and data centers can have existential consequences for companies. Recent incidents such as Russian and Chinese cyberattacks or software-related failures demonstrate the urgency of the situation. Critical infrastructure companies (KRITIS) such as energy and water suppliers, hospitals, banks, and transport companies are essential to life and the economy and are therefore particularly vulnerable targets.
The new European NIS 2 Directive, which will come into force in October 2024, aims to promote better and more comprehensive resilience against cyber threats. At the same time, the BSI (Federal Office for Information Security) has published information and regulations that are mandatory for operators of critical infrastructures.
This results in high IT security requirements for building management from both an economic and legal perspective. Legal requirements, risks, and opportunities have changed significantly. A technical article by Christian Wild, Managing Director of ICONAG-Leittechnik in Idar-Oberstein, provides information on the current legal regulations, highlights the greatest sources of risk and deficits in technical building management (TBM), and explains how BACnet contributes to implementation.
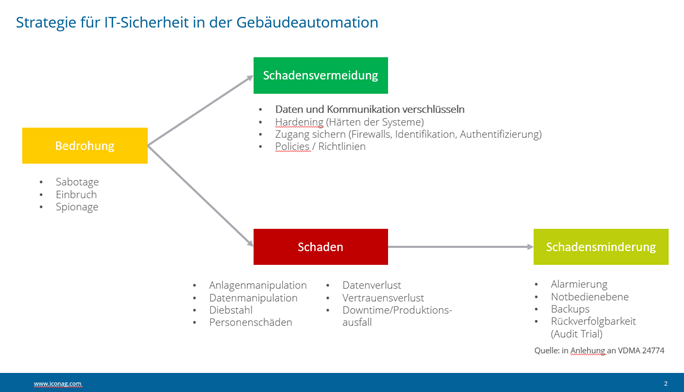
System malfunctions can occur internally and externally. Internal malfunctions affecting availability, integrity, authenticity, and confidentiality impact the fundamental operational reliability of the infrastructure. External malfunctions usually involve sabotage, espionage, or unauthorized access.
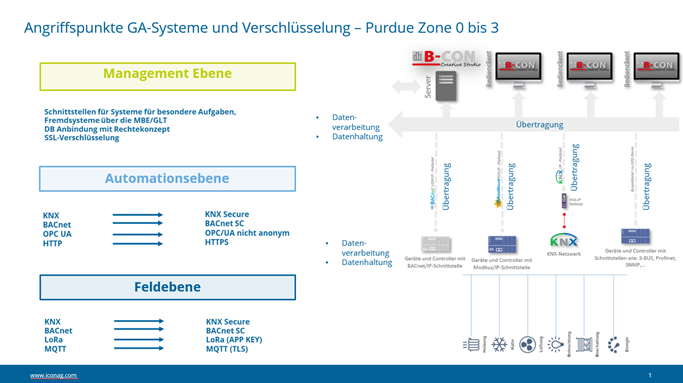
The usual points of attack on automation systems are primarily at the automation and management level of a building, rather than at the field level or higher levels of technical building management. This is why there is a particular need for action here.
Regulations for IT security in building automation
The fundamental regulations in Germany are the standards and the Basic Protection Compendium of the Federal Office for Information Security (BSI). The basic protection modules Infrastructure for Building Management (INF.13) and Building Automation (INF.14) are mandatory for federal authorities and operators of critical infrastructures (information available at www.bsi.de). The VDMA 24774 (2023-03) standard sheet describes the current requirements for IT security in building automation (guideline for building automation), and EU Regulation 2016/679 provides information on the General Data Protection Regulation for the protection of personal data in building automation.
Nevertheless, even building automation cannot offer 100% IT security. The specific precautions to be taken in building automation must be derived from a risk analysis for the respective use. The BSI Standards and Basic Protection Compendium lists the following risk situations as particularly significant for building automation:
• Inadequate planning of building automation, for example due to a lack of redundancy or the high complexity of the interaction between different trades.
• Incorrect integration of building services systems into building automation or incorrect configuration of building automation.
• Use of insecure systems and protocols in building automation, such as the “old” BACnet protocol, as well as KNX or ModBus.
• Manipulation of the interfaces between independent TGA systems and building automation (e.g., via a manipulated fire alarm that opens all doors).
Deficits in technical building management (TBM) as sources of risk
• Lack of IT security fundamentals for TBM planning, as operators are often not yet determined at the planning stage.
• Inadequate documentation in TBM leads to uncertainty about the status quo of IT security.
• Conscious or unconscious compromise of interfaces with TBM, especially when sensitive areas are connected to TBM, such as burglar or fire alarm systems.
• Inadequate monitoring of building services, meaning that system-critical malfunctions, for example, are not detected.
• Inadequate role and authorization management (e.g., multiple people sharing a user account).
Added to this are the long life cycles of building services systems, which require a particular degree of forward planning for GA systems and a strategic approach. The following specifications should therefore always be taken into account when planning GA systems.
Requirements for the planning of GA systems
⇒ Encrypted data transmission/communication (BACnet/SC, KNX-Secure, or similar).
⇒ Deactivation of all unnecessary services and accesses ex works (“hardened” devices and software), including documentation of the ports used.
⇒ Management software with functions for recording user activities (audit trail).
⇒ Acceptance of the GA system only with the latest firmware (automation stations) or software version (BBE, MBE), at least all security-relevant updates, in particular the latest Windows patches and the latest versions of the software systems used.
Requirements for the implementation and execution of building automation systems
⇒ Establishment of physically or virtually separate IP networks for building automation, including protection of particularly vulnerable network segments by firewalls.
⇒ Secure access for remote maintenance.
⇒ Definition of a backup concept for automation stations and management level, including instructions for recovery.
⇒ Physical security of switch cabinets, technical rooms, etc., including deactivation of USB or Ethernet access.
⇒ Malware protection and latest security patches for engineering tools.
⇒ Project-specific adjustment of access authorizations and change of passwords (especially on automation stations, BBE, MBE), activation of auto-logoff functions.
⇒ Hardening of systems by deactivating or deleting all unused services, physical access points, user accounts, processes, and programs (especially on automation stations, BBE, MBE), activation of auto-logoff functions.
⇒ Creation of work regulations and behavioral instructions for the permanent maintenance of IT security by the installer (SOP = Standard Operating Procedure).
⇒ Creation and handover of GA network documentation with model designations of the components, MAC addresses, installation location, and firmware version statuses.
⇒ IT security training for operators.
Requirements for operating GA systems
⇒ Individual user names and passwords.
⇒ Regular security-related updates/upgrades (especially for PCs, servers, and routers), ensuring that updates are downloaded exclusively from authentic, certified sources.
⇒ Regular backups of system programming, configuration, configuration changes to the MBE software, and stored operating data.
⇒ Ensuring compliance with work regulations and behavioral instructions, including regular updates to the IT security concept as part of GA system maintenance.
⇒ Regular IT security training.
Summary
Even in building automation, there is no 100% guarantee of data availability, integrity, authenticity, and confidentiality. However, a good level of security can be achieved by specifying and observing simple technical and organizational measures. The consistent use of BACnet is just one, albeit important, component in ensuring greater future security.
In summary, here are 5 tips:
1. Determine the protection requirements for each building based on a risk analysis. This must be done jointly by specialist planners, building owners, and operators.
2. Be aware that GA systems are particularly vulnerable in terms of IT security, with the greatest risks currently arising from the connection of building automation to the Internet, e.g., due to cloud computing.
3. Based on a security concept, establish specific IT security requirements for planning, implementation, and operation based on VDMA 24774. Against the backdrop of increasing cloud computing, encrypted protocols such as BACnet should also be required for new GA systems to be installed and for the renovation of existing GA systems.
4. Issue work regulations and behavioral guidelines (policies) for damage prevention and damage mitigation. Arrange for software maintenance and system maintenance to regularly close known security gaps.
5. During regular maintenance, check not only compliance with policies, but also that the security concept is up to date.
Relevance
Cyberattacks are a daily reality. An analysis by the digital association Bitkom in August 2024 revealed that 90 percent of German companies have already been victims of a cyberattack. Attacks on companies caused almost €267 billion in damage over the past twelve months. Forty-five percent of respondents said they could attribute at least one attack to China, followed by Russia with 39 percent. Around two in three companies see cyberattacks as a threat to their existence, significantly more than in previous years.
The extended NIS2 guidelines will apply from October 2024 and now also affect smaller companies, other industries, and suppliers of KRITIS operators.
Powered by ModuleStudio 1.3.2